Rare Kimsuky Leak Reveals Tactics and Infrastructure of North Korean-Linked APT
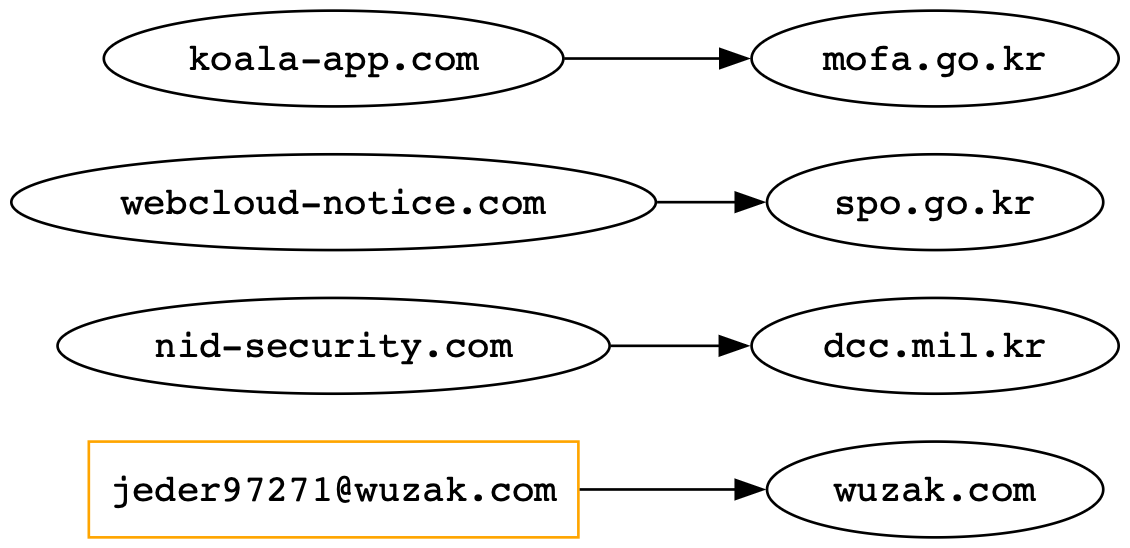
A rare security incident involving a data breach attributed to a North Korean-affiliated actor, dubbed “Kim,” offers unprecedented insights into Kimsuky (APT43) tactics, techniques, and infrastructure. The group focuses on credential-centric intrusions targeting South Korean and Taiwanese networks, blending Chinese-language tooling, infrastructure, and potential logistical support. The “Kim” dump, containing bash histories, phishing domains, OCR workflows, compiled stagers, and rootkit evidence, reveals a hybrid operation between DPRK attribution and Chinese resource utilization. The leaked data includes malware development, OCR parsing of Korean PKI and VPN documents, and reconnaissance targeting Taiwanese government and academic institutions. Analysts uncovered an advanced Linux rootkit employing syscall hooking and stealth persistence. The incident highlights the evolving capabilities of North Korean threat actors and their potential connections to Chinese resources.