Making Apple Watch Work with Android: An Open-Source Odyssey
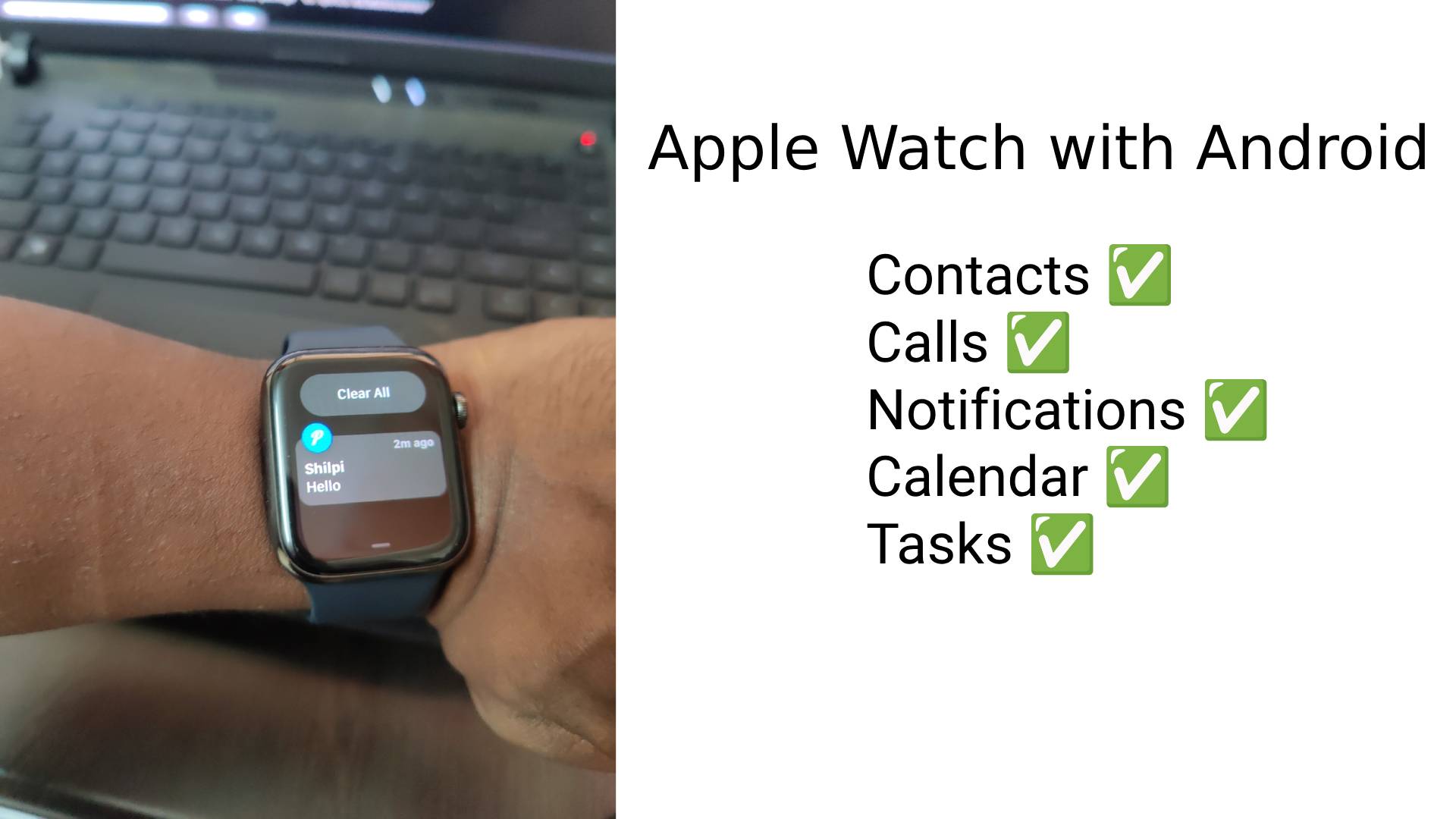
The author details their journey to connect an Apple Watch to an Android phone, bypassing Apple's walled garden. This involved using open-source apps, interoperable protocols, and third-party services, even requiring a secondary, home-based iPhone for initial setup. The author overcame challenges with notifications, calendar syncing, and contact integration, sharing their code on GitHub. This project highlights the power of open-source and the author's commitment to tech freedom, offering a compelling counterpoint to the closed ecosystems of tech giants.
Read more