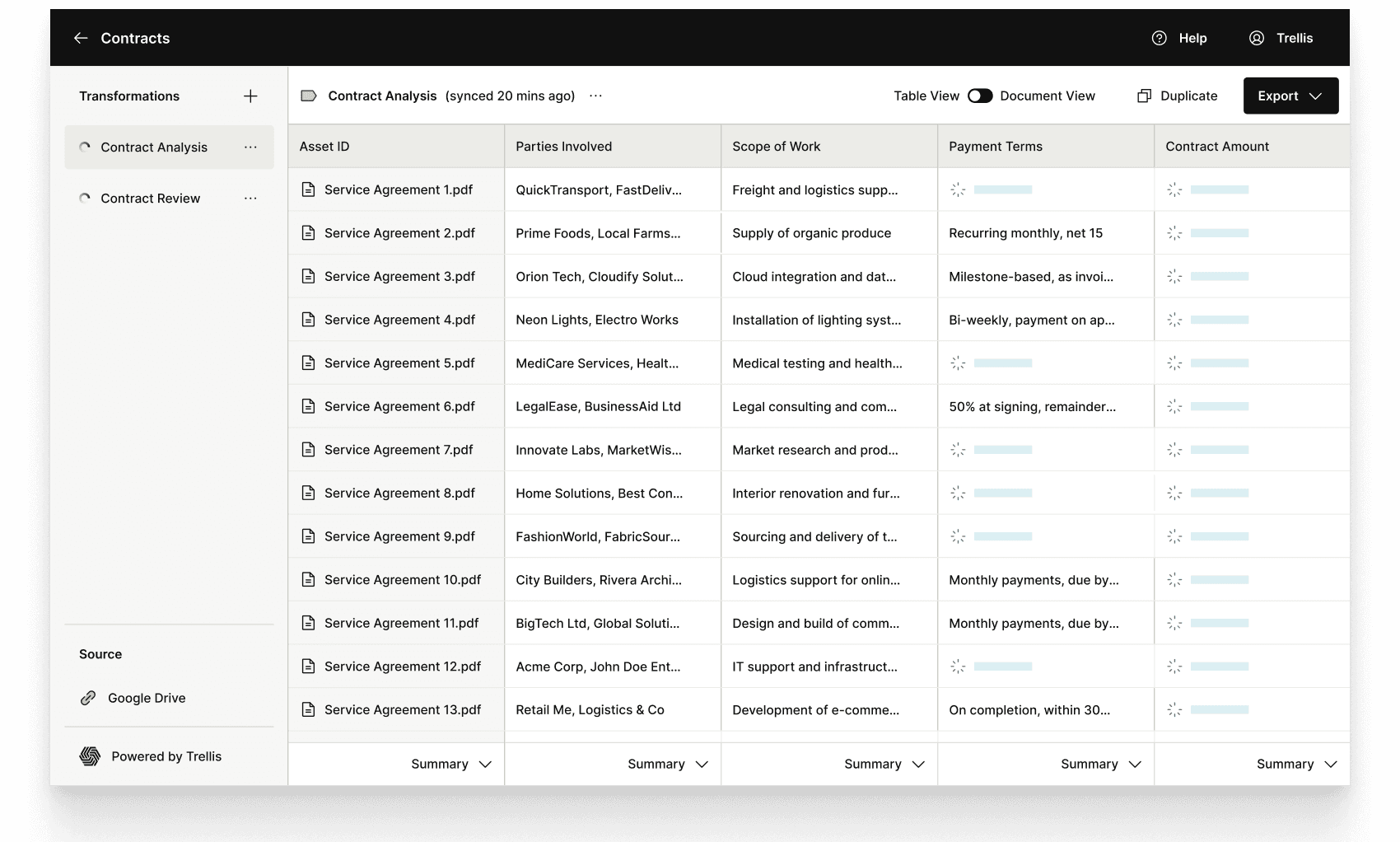
Stealthy VPN Backdoor Uses 'Magic Packets' to Evade Detection

Researchers uncovered a novel backdoor, dubbed J-Magic, infecting dozens of enterprise VPNs running Juniper's Junos OS. This backdoor leverages 'magic packets' embedded within normal TCP traffic, activating only upon receiving specific data patterns. To prevent unauthorized access, J-Magic employs an RSA encryption challenge-response mechanism. Its in-memory operation further hinders detection. The backdoor has been found in 36 organizations across various industries, including semiconductor, energy, manufacturing, and IT. The origin of the infection remains unknown.