OAuth 2.0: Securely Authorizing Third-Party App Access to Your Data
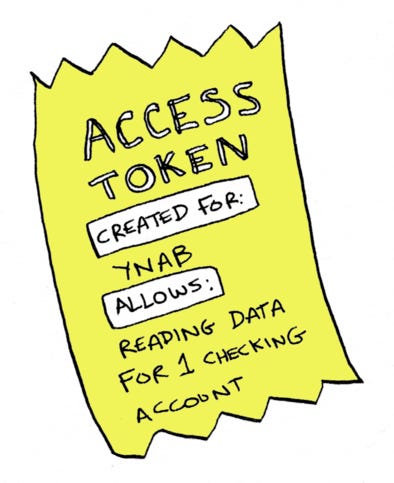
OAuth 2.0 is an authorization protocol allowing users to grant third-party apps access to their account data without sharing passwords. This article details the OAuth 2.0 workflow, including user authorization, authorization code retrieval, access token exchange, and emphasizes security measures like avoiding direct access token transmission in URLs. Key OAuth 2.0 terminology is explained, such as resource owner, OAuth client, authorization server, and resource server, along with front-channel and back-channel concepts. The article also covers PKCE for backend-less applications.
Read more