用开关笔记本电脑打摩尔斯电码 (github.com)
Open and Shut 项目可以让用户通过反复开关笔记本电脑来输入摩尔斯电码。该项目利用了 ACPI 事件和 xdotool 工具,将笔记本电脑开合动作转换为摩尔斯电码。
Kaskade:一款用于 Kafka 的文本用户界面 (github.com)
Kaskade 是一款基于 Textual 构建的 Apache Kafka 文本用户界面 (TUI),它允许用户在终端中以一种优雅的方式与 Kafka 交互和消费主题。Kaskade 提供了丰富的功能,包括主题管理、消费者视图、多种数据格式反序列化、Schema Registry 支持、Protobuf 反序列化支持等。用户可以通过命令行轻松使用 Kaskade 连接到 Kafka 集群,并执行各种操作。
ZeroMQ (zeromq.org)
ZeroMQ (ØMQ, 0MQ, zmq)是一个开源的通用消息传递库,它类似于嵌入式网络库,但实际上是一个并发框架。它提供了套接字,可以在进程内、进程间、TCP 和多播等各种传输方式中传递原子消息。ZeroMQ速度快,支持多种语言API,适用于构建可扩展的多核应用程序。
网页开发的混乱:过度依赖框架和库导致性能低下 (medium.com)

文章批评了现代网页开发过度依赖JavaScript框架和库的现状,尤其是React。作者认为这种过度依赖导致代码臃肿、性能低下、依赖管理混乱等问题,并以React、Webpack、Electron等为例证说明。作者建议开发者回归简洁,尽可能使用原生JavaScript或更轻量级的框架,并推荐了SvelteKit和Blazor等工具。
构建和扩展Notion数据湖 (www.notion.so)
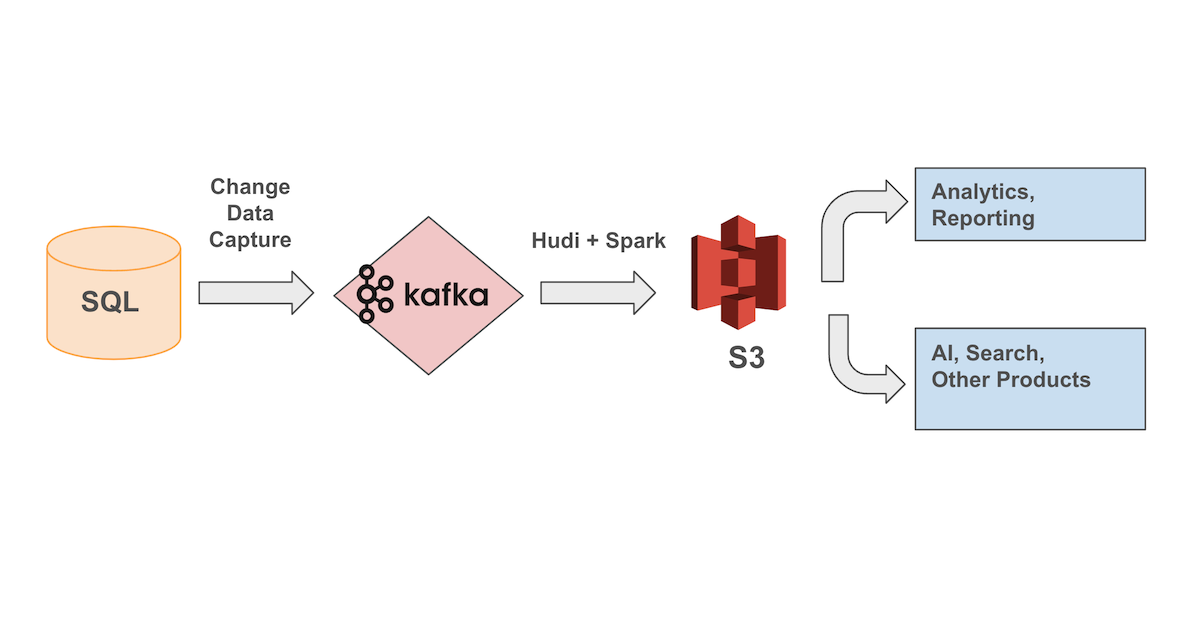
这篇文章讲述了Notion如何应对用户和内容增长带来的数据量激增挑战。Notion的数据量在三年内增长了10倍,每6-12个月翻一番。为了管理这种快速增长并满足不断增长的产品和分析需求,Notion团队构建并扩展了自己的数据湖。文章详细介绍了数据湖的设计决策、技术选型、扩展和运营经验,以及最终取得的成果:节省成本、提高数据新鲜度、为AI功能提供强大基础设施。
地球上大多数生命处于休眠状态 (www.quantamagazine.org)

最新研究发现,地球上大多数微生物和细胞都处于休眠状态,这是它们应对恶劣环境的一种生存策略。科学家发现了一种名为Balon的蛋白质,它可以迅速关闭细胞的蛋白质生产,使细胞进入休眠状态。Balon普遍存在于各种生物体中,并且可以快速地从细胞中插入或移除,使细胞能够快速进入或退出休眠状态。
Embark工作室开源基于Rust的渲染器Kajiya (medium.com)

游戏工作室Embark开源了其基于Rust语言开发的渲染器Kajiya,该渲染器支持光线追踪和实时全局照明等特性。Embark认为Rust非常适合图形编程,并希望通过开源Kajiya推动Rust在游戏开发领域的应用。
技术笔记:多态性shellcode (neugierig.org)
文章介绍了多态性shellcode的概念、作用和实现方式。多态性shellcode是为了避免被安全软件检测,其代码会不断变化,增加攻击识别的难度。文章以Metaspoit的“shikata ga nai” (SGN)为例,详细解释了其解码器的工作原理,以及如何通过改变寄存器、指令顺序和隐藏循环尾部等方式来实现代码的多态性。
更多网页,更少网络应用! (liberda.nl)
文章批评了网络应用程序日益占据网络主导地位的现状,指出网络应用程序过度依赖 JavaScript、体积臃肿、用户体验差等问题,并呼吁回归网页的本质,构建更加轻量、高效的网络体验。作者还批评了谷歌对 Chromium 的垄断以及网络标准制定过程中过于注重开发者体验而忽视用户体验的现象。
Adobe高管将Creative Cloud取消费用比作“海洛因” (www.theverge.com)
/cdn.vox-cdn.com/uploads/chorus_asset/file/23624357/acastro_STK124_03.jpg)
Adobe高管将Creative Cloud的提前取消费用比作“海洛因”,引发争议。联邦贸易委员会(FTC)指控Adobe隐藏费用并故意设置复杂的取消流程,用户对此表示不满。Adobe辩称其做法合法合规,并更新了订阅流程,用户可在30秒内取消订阅。此案的关键在于如何定义“简单”的取消流程,Adobe计划在法庭上挑战FTC的解释。
科学家发现一种可以强健骨骼的新激素 (www.ucsf.edu)

加州大学旧金山分校和加州大学戴维斯分校的研究人员发现了一种名为母体脑激素 (CCN3) 的新激素,可以增加骨密度和强度,并成功利用该激素帮助老年小鼠的骨折愈合。研究表明,CCN3 在哺乳期女性大脑中产生,可以弥补雌激素水平低导致的骨质疏松风险,未来可能用于治疗骨质疏松症和其他骨骼疾病。
FBI 尝试解锁特朗普集会枪击案枪手手机 (www.theverge.com)
/cdn.vox-cdn.com/uploads/chorus_asset/file/23982723/acastro_STK004_01.jpg)
美国联邦调查局正在努力解锁上周六在宾夕法尼亚州特朗普集会上向特朗普开枪的枪手的手机。调查人员希望通过手机获取更多关于枪手作案动机的信息。目前,手机已被送往弗吉尼亚州匡蒂科的 FBI 实验室,FBI 希望在那里能够绕过手机的密码保护。调查人员仍在调查枪手托马斯·马修·克鲁克斯的作案动机,目前还不清楚他的信仰和作案原因。
《音乐如何免费》: 从人性的角度揭示音乐盗版起源 (www.forbes.com)

这部纪录片剧集讲述了音乐行业如何从销售高价CD到濒临崩溃的历程。其中揭示了MP3技术的发明者并非推动其普及的主力,而是青少年将其用于盗版音乐文件。该片深入探讨了一群盗版者如何通过内部人士获取最新专辑和单曲,并展示了个人如何颠覆整个行业的可能性。
美英韩三国指控朝鲜黑客窃取军事机密 (www.scmp.com)

美国、英国和韩国7月26日发表联合声明,指控朝鲜黑客发起全球网络间谍活动,窃取机密军事机密,以支持其核武器计划。据称,这些被称为“安达列尔”或“APT45”的黑客隶属于朝鲜侦察总局,该机构于2015年受到美国制裁。该组织的目标包括美国国家航空航天局、多家国防和工程公司,以及位于德克萨斯州的兰道夫空军基地和佐治亚州的罗宾斯空军基地。美国司法部指控一名嫌疑人林正赫(音译)参与了针对美国计算机网络的攻击和洗钱活动,并悬赏高达1000万美元,以获取能逮捕他的信息。
Below MI - IBM i 安全研究 (silentsignal.github.io)
本文深入探讨了 IBM i 操作系统在机器接口(MI)层以下的运作机制,特别关注内存安全问题。文章首先介绍了IBM i 的单级存储模型和安全级别,然后详细分析了指针标记、类型指针和段边界检查等安全机制,并结合示例代码解释了如何绕过这些机制,最终实现任意代码执行。
当对象不再够用 (www.tonysm.com)
这篇文章探讨了面向对象编程(OOP)中对象的作用,特别是在大型系统中。作者认为,仅仅依靠对象来构建系统是不够的,还需要关注对象之间的消息传递和系统架构。作者建议将消息也视为对象,并使用类似发布/订阅的模式来管理对象之间的通信。此外,作者还讨论了抽象的重要性,认为合适的抽象可以简化系统模型,并以开普勒的椭圆轨道理论为例进行了说明。
SPF、DKIM 和 DMARC 简介:邮件安全标准详解 (bastion.tech)

随着网络钓鱼攻击日益猖獗,确保电子邮件安全至关重要。文章介绍了三种电子邮件安全协议:SPF、DKIM 和 DMARC,它们共同作用以减少垃圾邮件和网络钓鱼企图。SPF 验证发件人身份,DKIM 确保邮件完整性,而 DMARC 则根据 SPF 和 DKIM 结果执行策略,阻止不符合要求的邮件。文章还提供了配置这些协议的建议,并指导用户如何识别和处理可疑电子邮件。
鲜为人知的工具如何通过即时访问大量购房者数据席卷房地产行业 (therecord.media)

一款名为Forewarn的应用正在房地产行业迅速普及。该应用由数据代理公司red violet所有,它可以让房地产经纪人只需输入潜在客户的电话号码,就能立即获取他们的详细数据,包括犯罪记录、地址历史、财务状况等。Forewarn的支持者认为它是一个有价值的安全工具,而批评者则担心它会助长歧视,并在用户不知情的情况下对其进行大规模画像。
揭开衰老和发育的主控制器 (longevity.technology)

昆士兰大学的研究人员在理解衰老和发育的分子机制方面取得了重大进展,强调了基因调控元件及其与转录因子相互作用的关键作用。研究发现,一种名为AP-1的转录因子是决定基因活性从出生到成年再到老年转变的关键因素。AP-1通过激活成人基因并抑制早期基因的活性,在不同细胞类型中表现出持续的活性,这表明了衰老的基本机制。该研究为解决阿尔茨海默病、代谢紊乱和中风等与年龄相关的疾病提供了希望。
Wayland 热点工具 wlhc 介绍 (whynothugo.nl)
wlhc 是一款能够为 Wayland 桌面环境提供“热点”功能的小程序。它允许用户将屏幕的某个角落与一个命令绑定,当鼠标指针触及该角落时,wlhc 就会执行相应的命令。该程序利用 wlr-layer-shell 协议来检测鼠标是否触碰角落,尽管这种用法并非协议的初衷,但运行良好。
瑞安航空在美国法院赢得针对Booking.com的案件 (www.rte.ie)

美国法院裁定Booking.com未经授权访问瑞安航空网站部分内容,违反了《计算机欺诈和滥用法案》。瑞安航空表示,该裁决将有助于终止预订网站未经授权的屏幕抓取行为。瑞安航空近年来对未经授权转售其机票的第三方预订平台提起了一系列法律诉讼,称这些公司使用屏幕抓取软件查找和转售机票,增加了额外费用,并使航空公司难以联系乘客。
任天堂总裁表示,没有在其游戏中使用生成式人工智能的计划 (www.cnet.com)

任天堂总裁古川俊太郎在最近的投资者问答中表示,虽然生成式人工智能具有创造性,但该公司不打算在其游戏中使用该技术。古川认为,生成式人工智能存在知识产权问题,并且任天堂数十年来在为客户创造最佳游戏体验方面积累了专业知识,这些价值无法仅通过技术实现。
为什么意大利不再钟爱香菜? (www.atlasobscura.com)

香菜在意大利有着悠久的历史,曾在古罗马菜肴中广泛使用。然而,从某个时期开始,意大利人逐渐放弃了香菜,这与日耳曼部落的饮食习惯、香菜缺乏“异域风情”以及法国烹饪的影响等因素有关。如今,香菜被视为一种“异国情调”的食材,不再符合意大利人的烹饪习惯。
爪哇巨石之山 (archaeology.org)

本文主要介绍了印度尼西亚爪哇岛西部的巨石遗址Gunung Padang。该遗址由五个阶梯状的人造梯田构成,梯田上布满了由数百个棱柱形安山岩块组成的矩形巨石结构。学者认为,这些结构是当地巽他族人祖先在约2000年前建造的,是印尼最古老的阶梯式寺庙之一,也是了解该地区巨石文化的重要遗址。文章还探讨了Gunung Padang的建造目的、建造年代,以及与当地信仰和社会结构的关系,并将其与印尼群岛的其他巨石遗址进行了比较。
物理学家创造出世界上最难的迷宫 (www.sciencealert.com)
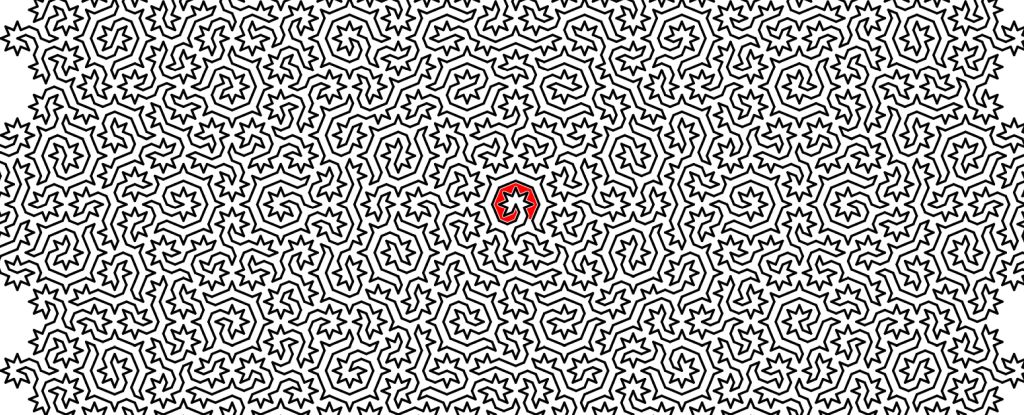
英国和瑞士的物理学家团队从分形几何和国际象棋中汲取灵感,创造出据说是世界上最难的迷宫。他们利用一种名为Ammann-Beenker瓷砖的模式,生成了称为哈密顿循环的路线,这种模式产生复杂的分形迷宫,据他们说,这种迷宫描述了一种被称为准晶体的奇异物质形式。这项研究的意义远远超出了娱乐的范畴,它有可能解决从复杂的路线寻找系统到蛋白质折叠等许多其他棘手的数学问题,甚至对碳捕获也有影响。
回顾我作为GNOME董事的时光 (blog.sonny.re)

本文是作者Sonny卸任GNOME基金会董事后的回顾。作者在任期内提出了去中心化GUADEC和开发资金两项建议,并已得到实施。作者还积极参与社区建设和解决冲突,并为基金会提供支持。作者希望GNOME未来能够解决功能障碍和冲突,为每个人创造更健康的环境。
美国孕产妇死亡率 alarming rate 上升 (news.northwestern.edu)

根据西北大学医学院的一项新研究,美国孕产妇死亡率正在以惊人的速度上升。研究发现,在 2014 年至 2021 年期间,美国孕产妇的总体死亡率几乎翻了一番,从 16.5 上升到 31.8,其中 2019 年至 2021 年增幅最大,从 18.9 上升到 31.8。值得关注的是,所有年龄组的孕产妇死亡率均有所上升,这表明年龄并非孕产妇死亡率上升的驱动因素。研究人员呼吁采取措施,更好地了解导致孕产妇死亡率上升的原因,并制定有效的预防措施。

