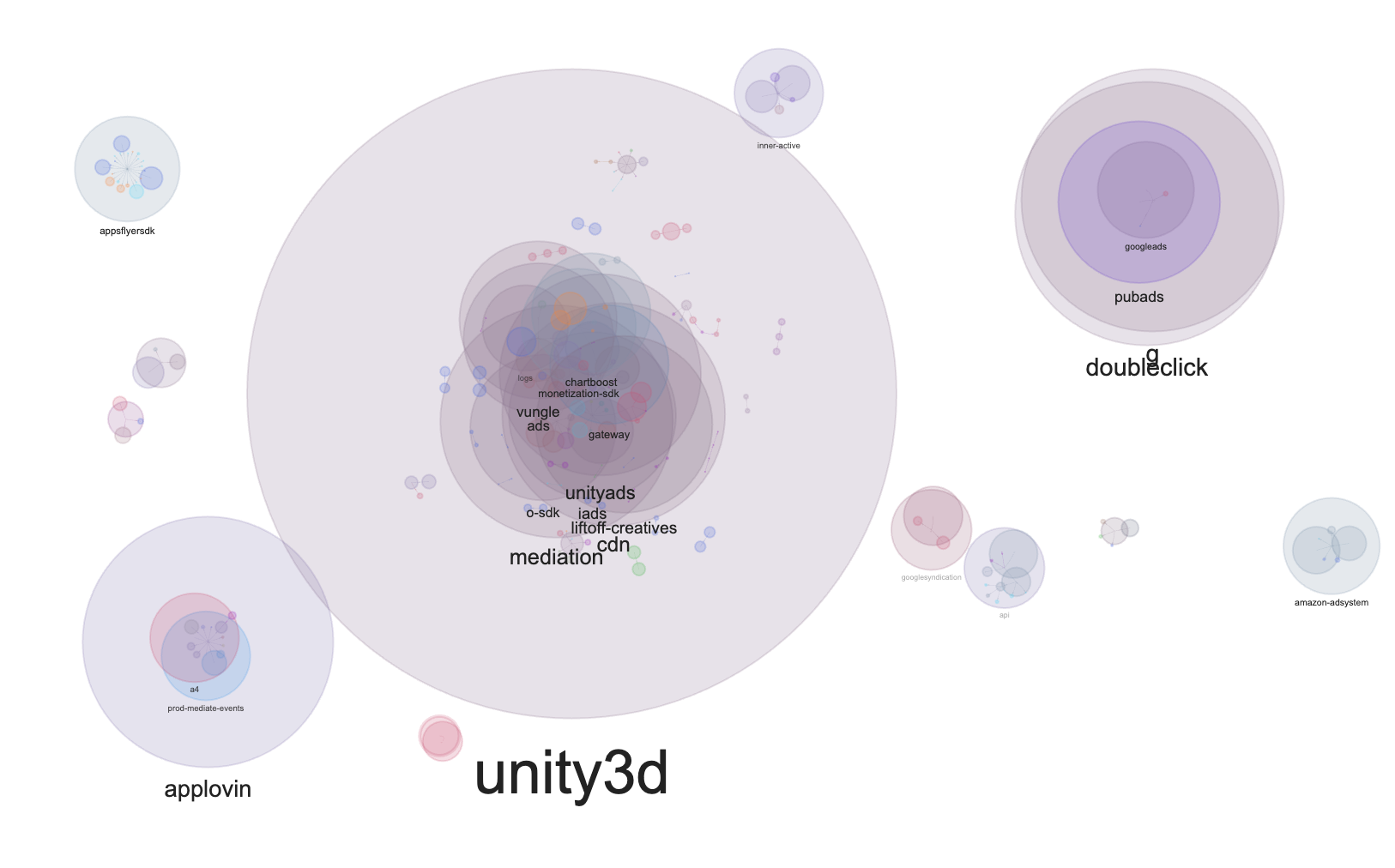
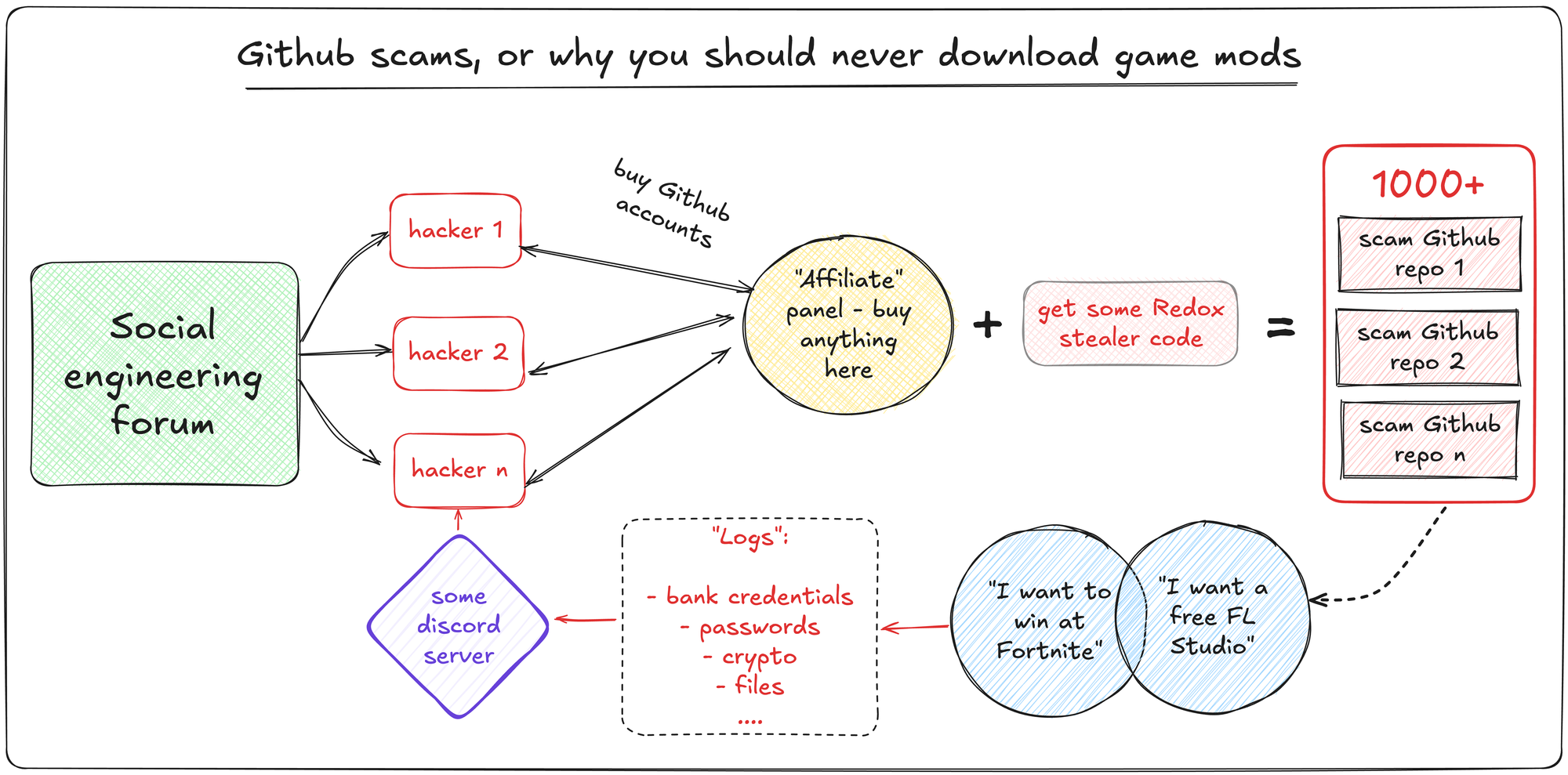
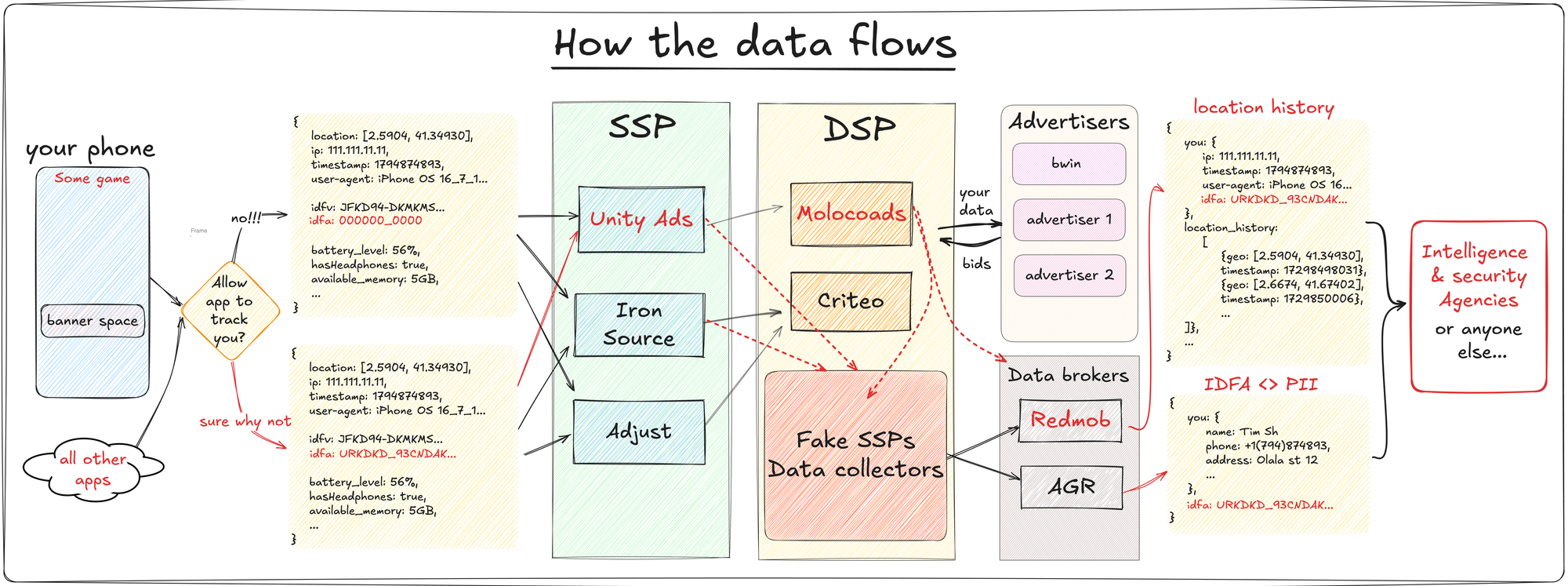
Running Claude Code Securely in Docker with VSCode Dev Containers
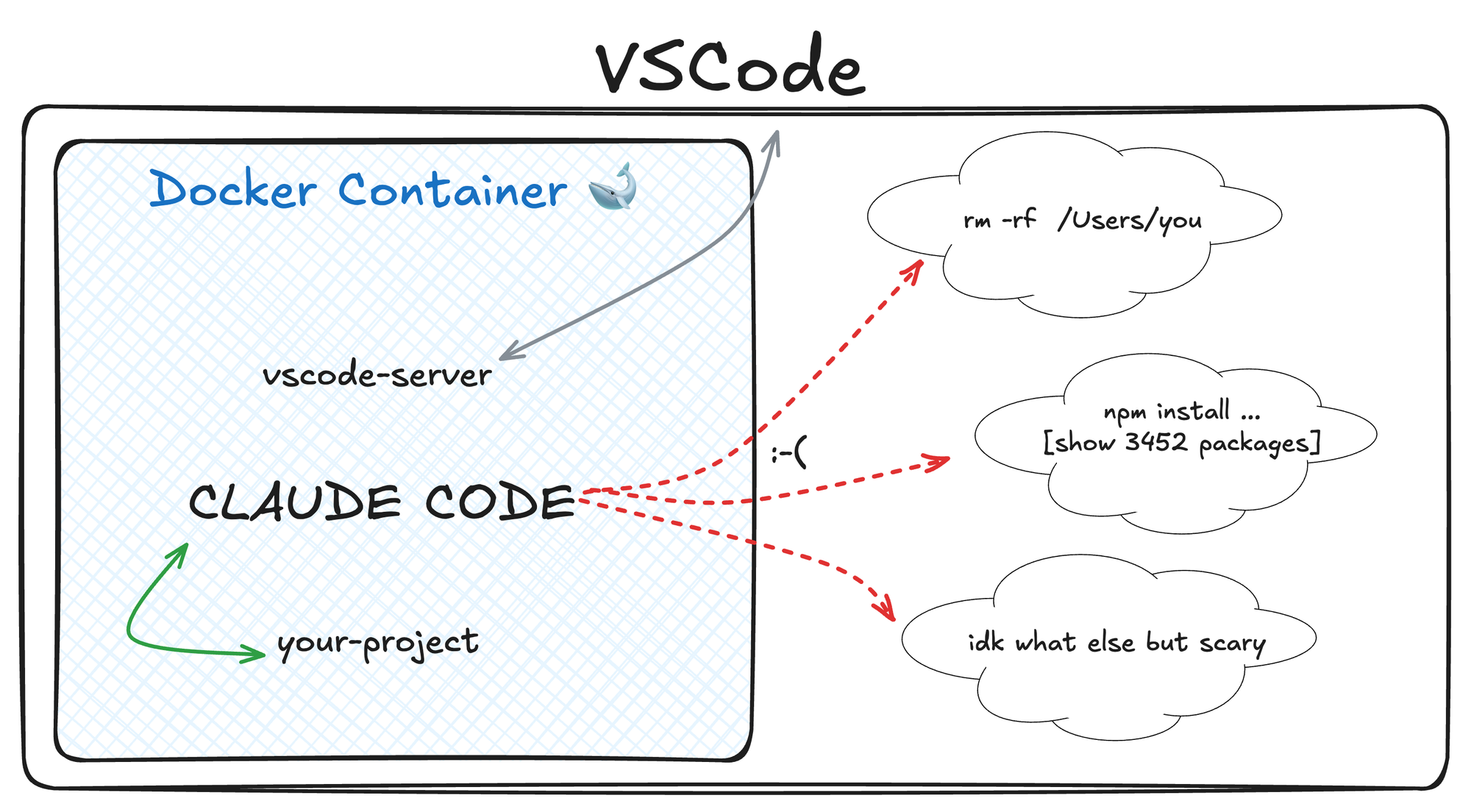
The author shares their experience transitioning from a less secure AI coding setup to running Claude Code in a Docker container using VSCode's Dev Container feature. Highlighting the security risks of running AI agents directly on the local machine, the author advocates for the isolated environment provided by Docker, limiting Claude Code's access to the filesystem. A detailed setup guide is provided, including creating a devcontainer.json file and using Fine-Grained access tokens for GitHub, making it easy for readers to replicate the setup.
Read more