Open-Source RAG Logger: RAG-logger Released
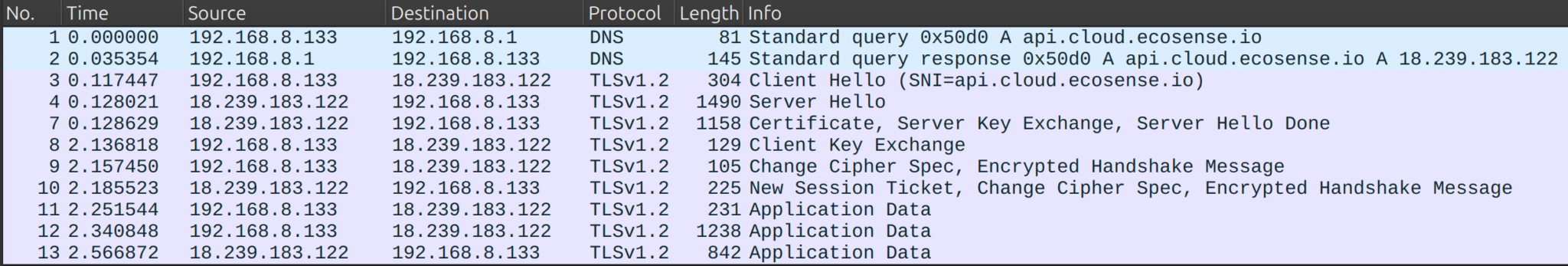
RAG-logger is an open-source logging tool designed specifically for Retrieval-Augmented Generation (RAG) applications. It offers a lightweight alternative to existing solutions, focusing on the specific logging needs of RAG pipelines. Key features include comprehensive logging of the entire RAG process, from query tracking and retrieval results (text and images) to LLM interaction recording and step-by-step performance monitoring. It utilizes a JSON-based log format, organizes logs daily, and handles automatic file management and metadata enrichment. A simple API allows for quick integration; for instance, `logger.log_query()` logs queries, `logger.log_retrieval()` logs retrieval steps, and `logger.log_llm()` logs LLM interactions.
Read more